The Diamond Model Cyber, a cornerstone of modern intrusion analysis, provides a structured approach to understanding adversary activity. Intelligence derived from sources such as MITRE ATT&CK, a globally recognized knowledge base of adversary tactics and techniques, significantly enhances the application of the Diamond Model. Security analysts at Cyber Command, leveraging diamond model cyber, can effectively analyze intrusion incidents and develop targeted defense strategies. Furthermore, the visualization capabilities of tools like Maltego allow analysts to graphically represent relationships between adversaries, victims, infrastructure, and capabilities, furthering insights gained from the diamond model cyber.
Crafting an Effective Article Layout: Diamond Model Cyber – Unveiling Intrusion Analysis Secrets
To effectively explore "Diamond Model Cyber: Unveiling Intrusion Analysis Secrets," focusing on the keyword "diamond model cyber," a structured article layout is crucial. This layout ensures clarity, readability, and comprehensive coverage of the subject.
Introduction: Setting the Stage
The introduction should capture the reader’s attention and clearly define the purpose of the article. It should introduce the diamond model cyber framework and its significance in intrusion analysis. Consider the following:
- Begin with a compelling opening statement about the challenges of modern cyber threat analysis.
- Briefly introduce the diamond model cyber as a solution for these challenges.
- State the article’s goal: to explain the diamond model’s structure, application, and benefits in detail.
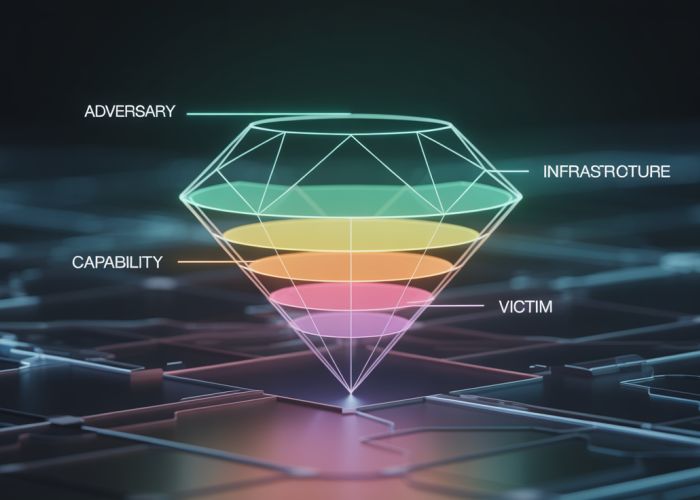
- Include a concise definition of the diamond model cyber. For example: "The diamond model cyber is a framework for analyzing cyber intrusions by representing events through four core features: Adversary, Capability, Infrastructure, and Victim."
Understanding the Diamond Model Cyber Framework
This section forms the core of the article, explaining each component of the diamond model in detail.
The Four Vertices: Deconstructing the Diamond
Each vertex represents a critical aspect of a cyber intrusion.
-
Adversary: The actor behind the intrusion.
- Who are they? (Nation-state, criminal group, insider threat)
- What are their motivations? (Financial gain, espionage, disruption)
- What resources do they possess? (Skills, tools, funding)
-
Capability: The techniques, tools, and procedures (TTPs) used by the adversary.
- What malware was used?
- What vulnerabilities were exploited?
- What methods were employed for lateral movement?
- Example: Phishing emails using malicious attachments.
-
Infrastructure: The physical or virtual systems used to conduct the intrusion.
- What servers, domains, or IP addresses were involved?
- What network configurations were utilized?
- Did they utilize any proxy servers?
-
Victim: The target of the intrusion.
- Who was targeted? (Specific individual, department, organization)
- What data was compromised?
- What systems were affected?
- What were the secondary victims?
Relationships and Edges: Connecting the Dots
The diamond model doesn’t just consist of the vertices; the connections between them are also vital. These edges represent the relationships between the four elements.
- Adversary ↔ Capability: What tools and techniques does the adversary typically employ?
- Capability ↔ Infrastructure: What infrastructure supports the use of this specific capability?
- Infrastructure ↔ Victim: How was the infrastructure used to target the victim?
- Victim ↔ Adversary: Is there a known relationship between the victim and the adversary (e.g., previous conflicts, targeted industry)?
Illustrate this with a simple diagram or table:
| Edge | Description | Example |
|---|---|---|
| Adversary -> Capability | Adversary utilizes specific tools for particular objectives | APT28 uses Mimikatz for credential harvesting. |
| Capability -> Infrastructure | Capability requires specific infrastructure to function | A botnet requires command-and-control servers. |
| Infrastructure -> Victim | Infrastructure is used to target a specific victim | A phishing campaign targets employees of a specific company using email. |
| Victim -> Adversary | A link between a victim and an adversary, possibly motives. | A government is targeted by a rival nation-state for espionage. |
Applying the Diamond Model in Intrusion Analysis
This section should detail how the diamond model can be used in practice.
Steps in Applying the Diamond Model
-
Data Collection: Gather as much information as possible about the incident. (Logs, network traffic, endpoint data, threat intelligence).
-
Vertex Identification: Identify the Adversary, Capability, Infrastructure, and Victim involved. This might be an iterative process as more information is gathered.
-
Relationship Mapping: Connect the vertices to represent the intrusion’s flow.
-
Event Pivot: Use the completed diamond to pivot to other related events, identify patterns, and predict future attacks.
Benefits of Using the Diamond Model Cyber
Use a bulleted list to highlight the advantages.
- Improved Visualization: Provides a clear visual representation of complex intrusions.
- Enhanced Understanding: Facilitates a deeper understanding of attacker motivations and tactics.
- Better Communication: Simplifies communication of intrusion details to stakeholders.
- Effective Pattern Recognition: Aids in identifying patterns and connections across different events.
- Proactive Threat Hunting: Enables more proactive threat hunting and mitigation strategies.
- Intelligence Sharing: Facilitates more effective threat intelligence sharing.
Real-World Examples: Case Studies
Include one or two brief case studies where the diamond model was used to analyze a real-world intrusion. These examples should illustrate how the model helped analysts uncover key information and improve their response. Briefly describe the incident and highlight which elements of the diamond model were most crucial in resolving the issue. For example:
- Case Study 1: Ransomware Attack on a Hospital: Analyze how the diamond model helped identify the ransomware group, their methods of entry, and the affected systems.
- Case Study 2: Data Breach at a Retail Company: Explain how the model was used to trace the exfiltration path, identify the compromised data, and attribute the attack to a specific actor.
Diamond Model Cyber: Frequently Asked Questions
This FAQ clarifies common questions about the Diamond Model and its application to cyber intrusion analysis.
What exactly is the Diamond Model of Intrusion Analysis?
The Diamond Model is a framework for understanding and analyzing cyber intrusions. It visualizes an event as a diamond shape connecting Adversary, Capability, Infrastructure, and Victim. This structure aids in tracking relationships and identifying patterns to understand the attack lifecycle.
How does the Diamond Model Cyber help with intrusion analysis?
By mapping intrusion events to the Diamond Model, analysts can uncover previously unknown relationships and commonalities between different incidents. This allows them to build more comprehensive threat intelligence and better anticipate future attacks. For example, tracing who the adversary is, their tools and infrastructure, and which victims are targeted.
What are the four core features of the Diamond Model?
The four core features are: Adversary (who is behind the attack), Capability (the tools and techniques used), Infrastructure (the systems supporting the attack), and Victim (the target of the attack). Effective use of the diamond model cyber depends on accurately identifying and connecting these core features.
Can the Diamond Model be used for proactive security measures?
Yes, by analyzing past intrusions using the Diamond Model, organizations can proactively identify vulnerabilities, improve threat detection, and strengthen defenses. Understanding adversary tactics and infrastructure allows for more targeted security investments and improved incident response planning based on diamond model cyber analysis.
So, there you have it – a glimpse into the power of the diamond model cyber! Hopefully, this gives you a solid foundation for digging deeper and making your digital world a little more secure. Happy analyzing!